Securing Code from All Angles: How SAST, DAST, and SCA Shape the Future of Application Security
Introduction
As digital transformation accelerates, businesses are increasingly reliant on software to deliver services, manage data, and connect with customers. While this offers numerous benefits, it also comes with significant risks, particularly when it comes to application security.
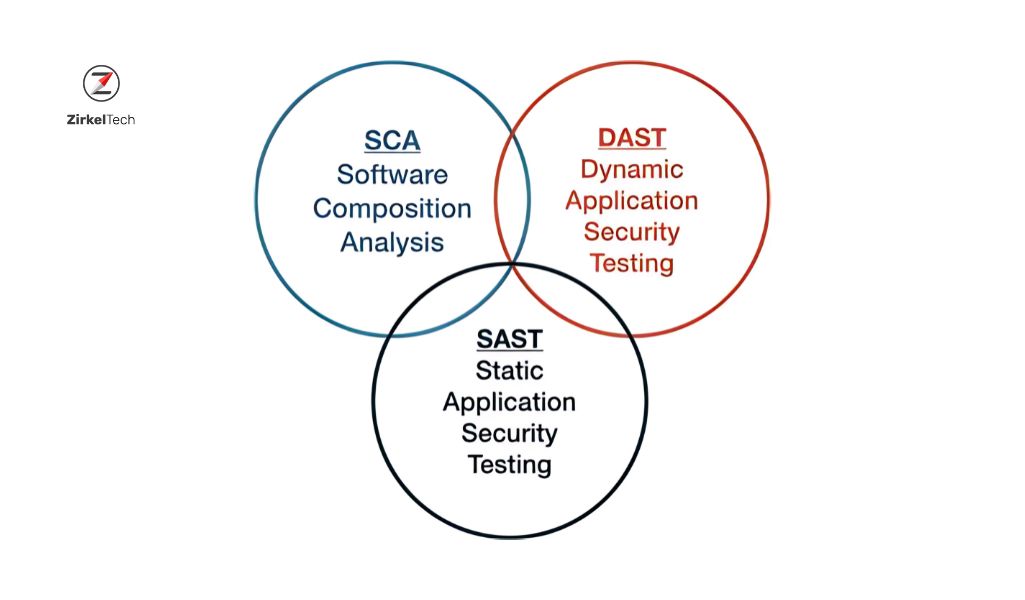
Protecting application security is vital for identifying weaknesses and addressing them proactively, preventing potential exploitation by cyber threats. In this context, three practices—Static Application Security Testing (SAST), Dynamic Application Security Testing (DAST), and Software Composition Analysis (SCA)—form the backbone of a robust application security strategy.
Each of these methods plays a critical role in securing applications, identifying flaws, and helping development teams address them at various stages of the software development lifecycle. In this blog, we’ll explore what these practices involve, their significance, and how they will evolve in the coming years to meet future challenges.
Breaking Down the 3 Pillars of Application Security
Let’s dive deeper into each of the three pillars:SAST, DAST, and SCA and understand how they contribute to the overall security of an application.
1. Static Application Security Testing (SAST): Preventing Vulnerabilities from the Start
SAST involves scanning the source code of an application before it's executed, allowing developers to identify and fix vulnerabilities early in the development process. It is a proactive approach to security, designed to catch potential vulnerabilities early in the development cycle—before the code is compiled or deployed. The process allows security teams to review the application’s source code or binary code to identify flaws such as code injection, buffer overflows, and other types of vulnerabilities that could be exploited.
How SAST Works:
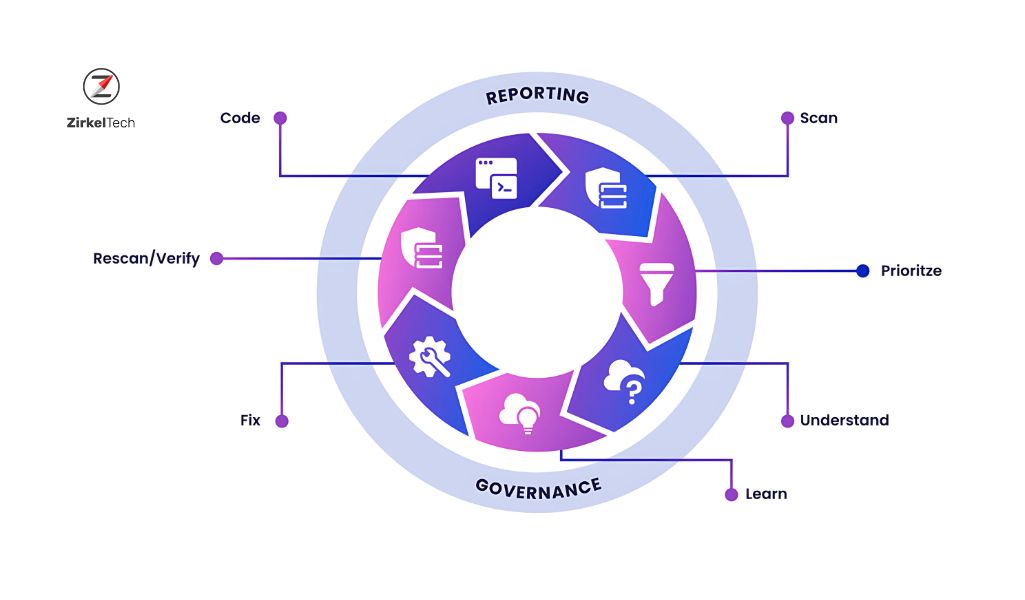
Why It’s Important:
• Early Detection: By identifying flaws during the development process, SAST allows developers to fix issues early, saving both time and money.
• Cost Efficiency: The earlier a vulnerability is detected, the cheaper it is to resolve.
• Automated Integration: Developers get instant feedback on their code, which allows them to address issues before they affect the final product.
2. Dynamic Application Security Testing (DAST): Uncovering Vulnerabilities Through Real-Time Analysis
DAST is a complementary method to SAST and focuses on testing the application while it’s running—whether in a staging environment or in production. It simulates real-world attacks, such as SQL injection or cross-site scripting (XSS), to identify vulnerabilities that only appear when the application is live and processing data.
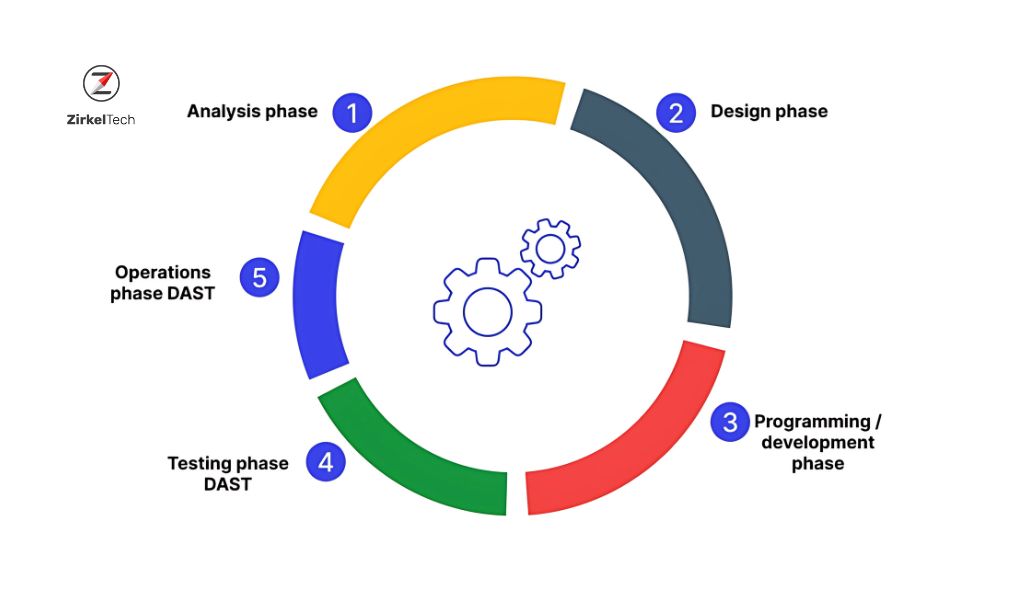
How DAST Works:
image
Why It’s Important:
• Real-World Testing: Since DAST tests a live, running application, it can detect issues that wouldn’t be visible in the code itself, such as vulnerabilities in business logic or runtime issues.
• Simulated Attacks: By mimicking real attack scenarios, DAST gives developers insight into how attackers might exploit the app in a production environment.
• Holistic Security: DAST doesn’t just focus on the code but looks at the overall functioning of the application in a dynamic environment, making it a crucial complement to SAST.
3. Software Composition Analysis (SCA): Securing Third-Party Libraries and Dependencies
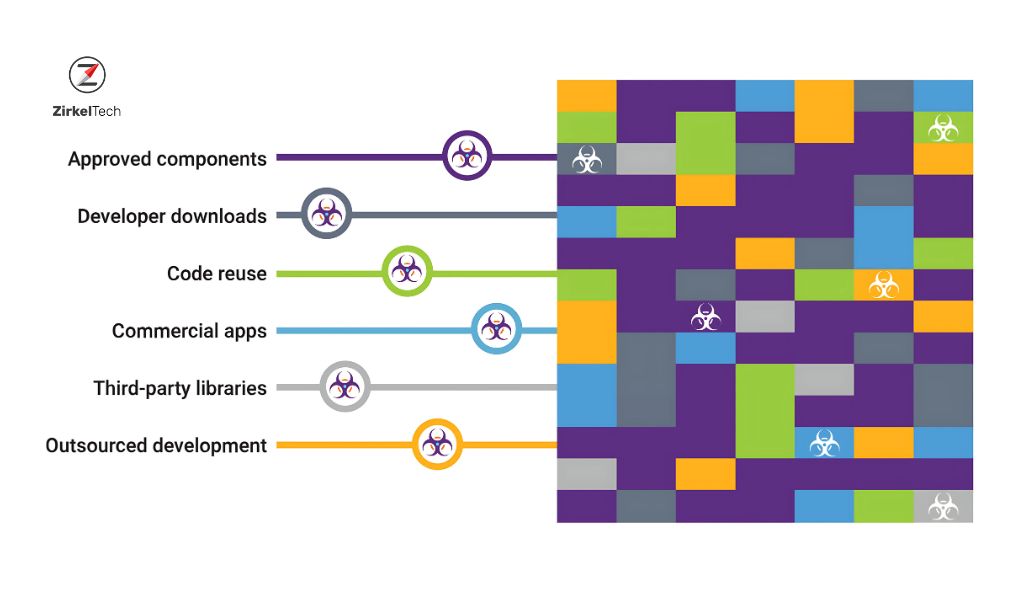
Modern applications are rarely built from scratch; they typically rely on a wide range of third-party libraries, open-source components, and pre-built services to speed up development. However, these external components introduce security risks, particularly if they contain known vulnerabilities.
SCA tools scan the third-party dependencies used in your application to identify any security vulnerabilities or licensing issues associated with those components. They provide insight into which libraries are outdated, which have known vulnerabilities, and which need to be updated or replaced.
How SCA Works:
image
Why It’s Important:
• Supply Chain Security: Many modern applications are built using libraries and components developed by third parties. SCA ensures that these external dependencies don’t introduce security vulnerabilities.
• Proactive Monitoring: SCA tools alert you to vulnerabilities in real time, allowing you to replace or update at-risk libraries before they can be exploited.
• Compliance and Licensing: SCA also helps manage licensing issues by ensuring that you use open-source components that comply with your organization’s policies.
Looking Ahead: How the 3 Pillars of Application Security Will Evolve
As the technology landscape shifts and new challenges emerge, the practices of SAST, DAST, and SCA will continue to evolve. By 2025, we can expect advancements that make these tools even more powerful, automated, and integrated into the development lifecycle.