Introduction
In the current digital era, the importance of software security has reached unprecedented levels. As technology continues to evolve and businesses become increasingly reliant on digital systems, the need to protect software from potential threats. With cyberattacks growing in frequency and sophistication, ensuring robust security measures in software development, deployment, and maintenance is essential for safeguarding sensitive data, maintaining user trust, and protecting an organization’s reputation. One of the most effective ways to reduce the risk of breaches and maintain software integrity is through regular source code audits. These audits are essential in identifying vulnerabilities, securing sensitive data, and improving the overall performance of applications across web, desktop, mobile, embedded, and cloud environments.
This blog explores the importance of source code audits for preventing cybersecurity threats, how to conduct them effectively, when to perform them, and the long-term benefits they offer organizations.
What is a Source Code Audit?
A source code audit involves thoroughly reviewing the underlying code of a software application to uncover security weaknesses, logic errors, performance issues, and areas of non-compliance. These audits are not limited to websites but also extend below:
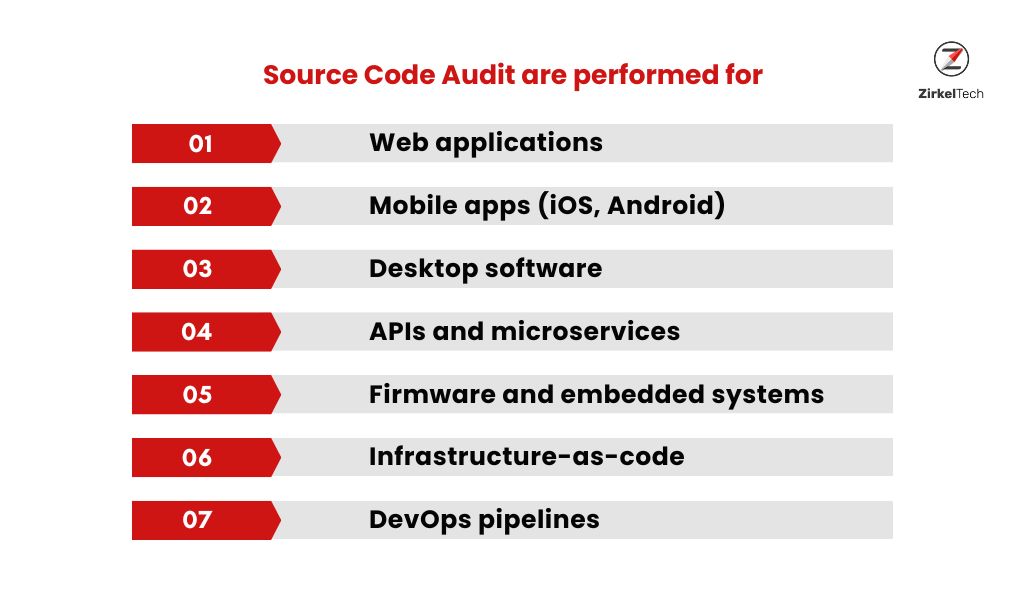
During a source code audit, both automated tools and manual review are employed to uncover below issues
• SQL injections
• Cross-site scripting (XSS)
• Hardcoded credentials
• Insecure configurations
• Use of outdated or vulnerable libraries
• Misuse of cryptographic functions
Regular audits offer a proactive security layer, ensuring your systems are better protected against evolving threats.
Why Regular Source Code Audits Are Essential

1. Early Identification of Vulnerabilities
Attackers exploit vulnerabilities in all types of codebases, not just web-facing ones. Source code audits help detect and eliminate these weaknesses before they are exploited in the wild.
2. Managing Risk from Open-Source and Third-Party Dependencies
Virtually all software uses third-party libraries. If these are outdated or unpatched, they can introduce critical vulnerabilities. Audits help manage and mitigate this risk.
3. Improving Developer Practices Across the Stack
Secure development practices differ depending on whether the system is mobile, web-based, or embedded. Code audits highlight bad practices and promote adherence to security principles like input validation, least privilege, and secure defaults.
4. Preventing Compliance Failures Across Environments
Whether your application handles healthcare data (HIPAA), processes payments (PCI-DSS), or manages personal data (GDPR), audits ensure that your code meets required legal and regulatory standards.
Source Code Audit Tools
Here’s a list of popular source code auditing tools:
1. Veracode
2. SonarQube
3. Checkmarx
4. Fortify
5. OWASP Dependency-Check
6. Pylint
7. GitHub Advanced Security
8. Flake8
How to Perform a Source Code Audit
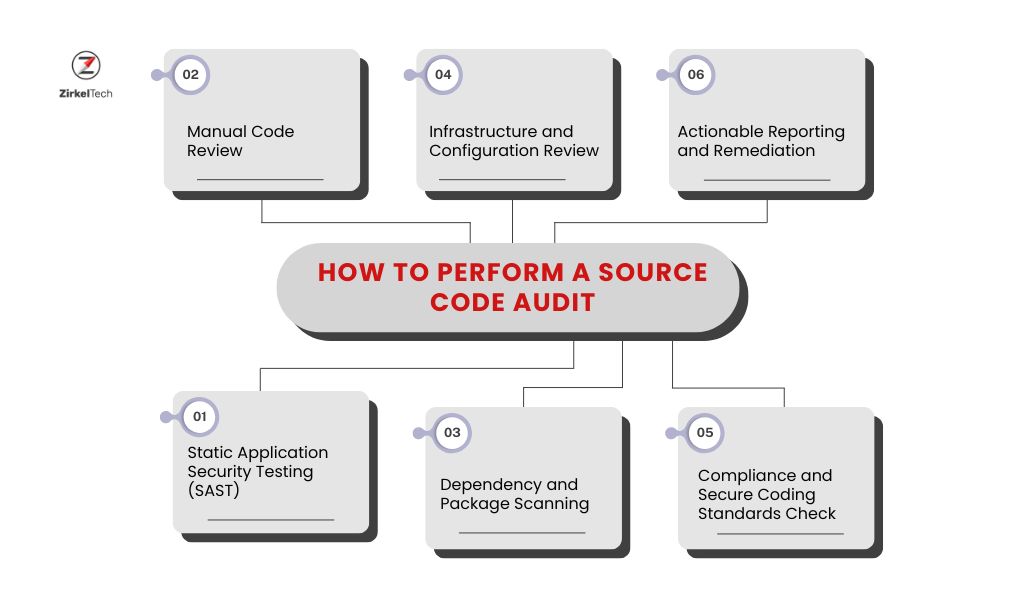
1. Static Application Security Testing (SAST)
Use tools like SonarQube, Checkmarx, or Veracode to detect vulnerabilities in the source code without execution. These are essential for any software language—from JavaScript and Python to C++ and Swift.
2. Manual Code Review
Automated tools frequently miss logic errors and vulnerabilities associated with business logic. Manual review by security experts adds human insight and catches subtle issues like insecure authentication flows or role mismanagement.
3.Software Composition Analysis (SCA)
Use SCA tools like Snyk, OWASP Dependency-Check, or WhiteSource to identify known vulnerabilities in open-source dependencies. These tools also help track outdated packages and licensing risks, ensuring your software supply chain is secure and compliant.
4. Dynamic Application Security Testing (DAST)
Once your application is running, use DAST tools such as OWASP ZAP, Burp Suite, or Acunetix to simulate real-world attacks. DAST identifies vulnerabilities that only appear during execution—like improper session handling, cross-site scripting (XSS), or broken authentication mechanisms—by observing application behavior from an external perspective.
5. Infrastructure and Configuration Review
For Infrastructure-as-Code (IaC) and deployment scripts, use tools like Terraform Sentinel or KICS to audit security configurations such as open ports, excessive permissions, or weak IAM policies
6. Compliance and Secure Coding Standards Check
Ensure that your code aligns with standards such as OWASP ASVS, NIST, and ISO/IEC 27001. This also includes checking cryptographic implementations, session handling, and user input validation.
7. Actionable Reporting and Remediation
A high-quality audit delivers clear findings and prioritized recommendations—what to fix, how to fix it, and how to prevent it in the future.
When to Perform a Source Code Audit
• Before Product Launch: Detect and resolve vulnerabilities before release.
• After Major Updates: Ensure changes haven’t introduced regression or new risks.
• Periodically (e.g., Quarterly or Biannually): Stay ahead of threats and evolving code.
• When Integrating New Libraries or Services: Ensure that external code does not introduce risk.
• After a Security Incident: Following a security incident, conduct a post-mortem audit to identify the underlying causes
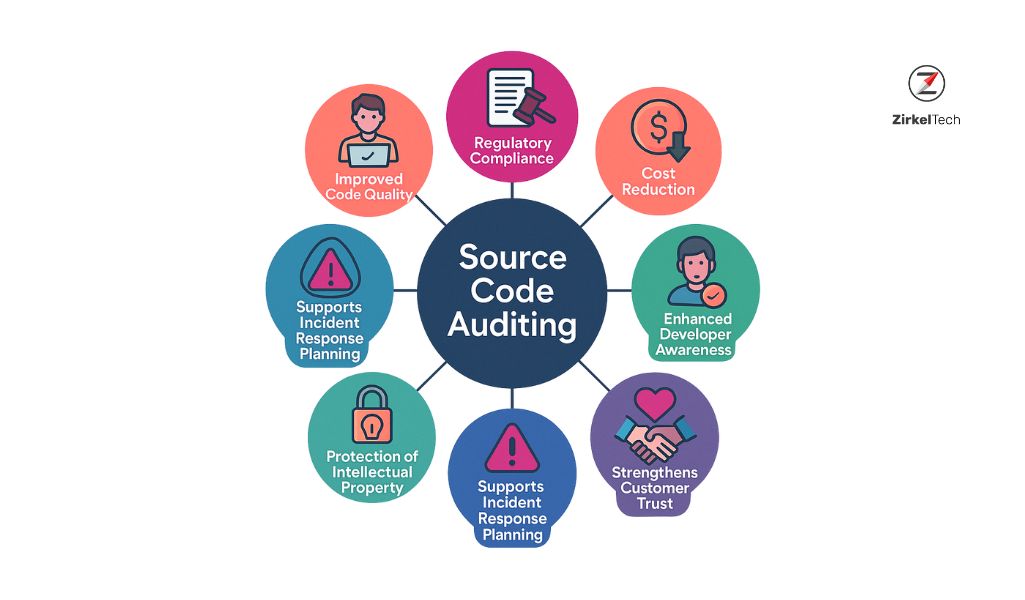
Benefits of Regular Source Code Audits